Virtual data rooms save businesses a lot of time and effort in their deal-making, while providing participants with all the tools necessary for efficient teamwork, streamlined due diligence, and a secure space for keeping confidential information.
This guide will tell you about the challenges of virtual data room setup, provide efficient steps on how to set up a data room properly, and offer some of the best practices to maximize data room usage.

Challenges related to setting up a virtual data room
Although unsurpassed security and intuitiveness come naturally to virtual data rooms, teams may still face challenges in selecting and setting up the software. Therefore, you should know the primary concerns to deal with them successfully.
- Compliance with regulations. The biggest advantage of compliance is that it lessens the possibility of fines, penalties, legal proceedings, or the closure of your company. For instance, if you disregard safety precautions, you risk receiving a significant fine from the authorities.
The more advanced the data room software, the more compliance you can benefit from, regardless of industry. Typically, the most secure online repositories comply with the GDPR, ISO/IEC 27001, SOC, and HIPAA. - User adoption. Besides knowing how to create a data room, you also need to consider things determining fast and smooth user adoption. Specifically, easy onboarding is possible if the data room interface, document navigation, and collaboration tools are intuitive.
To prevent performance degradation due to poor user adoption, test the software for ease of use, assign superusers to help others, conduct system user training, and provide post-implementation support. Some data room services assist teams in onboarding and further virtual data room use 24/7. - Permission settings. Data rooms allow you to grant access so that everyone can only see the documents they need. Thus, unlimited users can work on your platform without data security and integrity risks. Besides, you can always edit folder and file permissions later as needed. Administrators can set permissions for group members, parent folders, and more.
The challenge is that errors in the access rights settings can cause leaks and financial losses. Fortunately, providers allow looking at the data room through the eyes of another user with the user security impersonation feature.
Steps involved in setting up a data room
A virtual data room is surely a secure environment for storing and exchanging confidential documents and project management during due diligence and other complex deals. However, the solution’s effectiveness largely depends on how well you set it up.
So, how to prepare your data room in a way that brings maximum benefit? Just follow the steps below and get what you need.
1. Choose a virtual data room provider
Although VDR systems follow the same setup procedures, not all vendors have the same extra features, cost, or customer support options. It’s essential to pick a vendor that will fit your needs perfectly. The choice is rather vast, but it’s not that hard to make the right decision if you compile a shortlist of a few companies that best suit your business needs. Here are the criteria you can use when looking for a data room provider:
- Your industry. While there are a lot of versatile vendors, begin with brands that offer tailored solutions for companies from your field of operation to make sure the data room will have all the required certificates and features.
- The functions you need. While some businesses will be fine without advanced features such as customization and a built-in AI, others might feel restrained if a virtual data room lacks specific tools.
- The budget. It’s important to have additional tools on board, the bill for the data room shouldn’t be a burden for your company.
- Reviews. Providers will always tell all the best things about their product. Dive into real reviews and customer testimonials to see the bigger picture.
And once you find that perfect fit, don’t rush it. First, use the trial period or a demo version a provider offers to see if the software truly suits your needs.
2. Prepare the documents
Today, most businesses have their sensitive documents already digitized. For such companies, it won’t be an issue to prepare the files for the upload and figure out which ones should go inside the data room.
However, you should double-check anyway whether some physical papers are left — if you think you might need them in your data room, digitize them. Ensure all the documents are up to date, and if they were scanned, check for all the information to be perfectly visible.
Since most data room providers would allow users to create several workspaces, you must give different projects clear and sound names that won’t let you mix them up. Ideally, you want to have a separate workspace for the internal document maintenance if you’re going to use a virtual data room, not only during deals. If you have such a workspace in your VDR, it’s vital that both you and your employees can tell it apart from other projects so that no one gives access to third parties to highly confidential files.
3. Upload and organize files
Modern data rooms offer a drag and drop feature that allows users to upload documents in bulk without hassle. Using this function for your data room setup, you can move the whole file and folder structure hierarchy if you have one established on your device already. The virtual data room will then index them automatically, and you’ll have a ready-to-use workspace.
Moreover, working with documents will be swift and smooth thanks to the document viewer, allowing you to view text-based documents and Excel files directly on the platform.
Also, you can create a file structure in the VDR to organize and classify documents. For this, create separate folders to group the documents when uploading files. For example, you could give your folders the following names:
- General corporate documents
- Capital stock and securities
- Finances and taxes
- Physical property and assets
- Intellectual property
Of course, the kinds of documents for data room folder structure will differ depending on whether you need it for a due diligence process or a real estate transaction. This structure is an excellent guideline for your workspace organization if you’re using a data room for document maintenance.
4. Customize the interface, emails, and agreements
Some providers will let you customize the virtual data rooms and invitation emails with your corporate colors and logo. Use this feature to create a smooth experience for third parties and make a nice impression. Some vendors also allow users to customize non-disclosure agreement invited parties will have to sign before accessing the data room software. It’s an important feature because these agreements let you protect your documents even better.
Also, advanced providers usually offer features to customize watermarks with colors and patterns to your taste. In addition, with the best software, you can customize headers and footers for PDF files that may be downloaded or printed.
5. Add employees
Depending on the virtual data room pricing you chose, you can add a certain number of administrative users to the data room. Determine who you can trust the integrity of sensitive information and add these team members to the workspace. You can then invite users who don’t need to have control over papers to work with them — you can give such users view-only access permissions.
As for file permissions, they may differ depending on the provider but some examples of common permissions include viewing, downloading original, downloading, and editing:
- Viewing – users can view files with a watermark
- Downloading original files – users can view, print, and download original unwatermarked files
- Downloading – users can print and download watermarked documents
- Editing – users can edit index, upload documents, move, overwrite, rename, and delete files
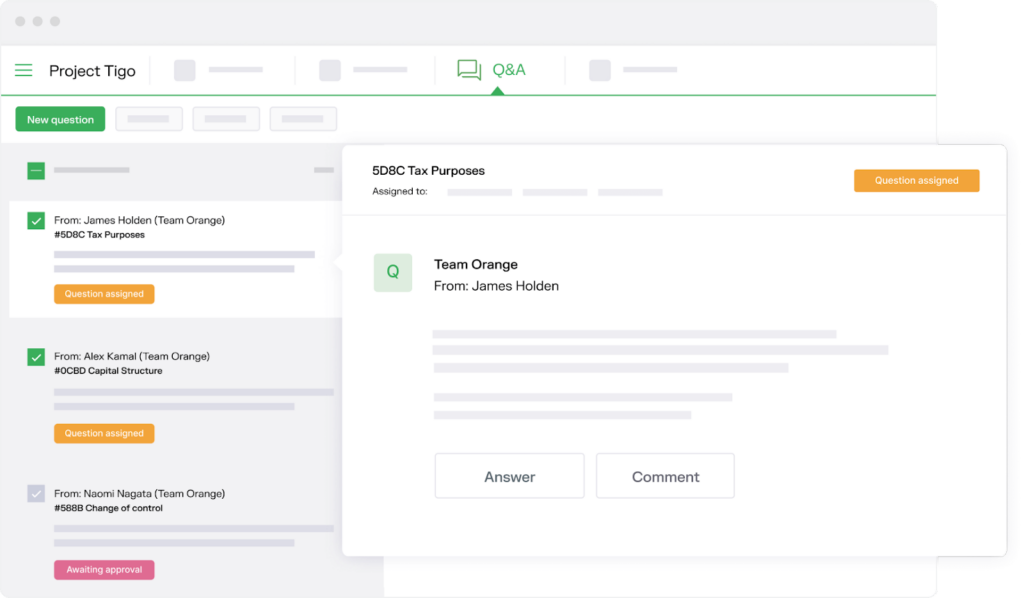
6. Fill in the Q&A section
This feature allows you to answer all the frequently asked questions before the deal to create some kind of knowledge base. Then you can assign someone to be responsible for the Q&A section during the agreement. This person will have to answer all the new questions from third parties as quickly as possible to accelerate the deal.
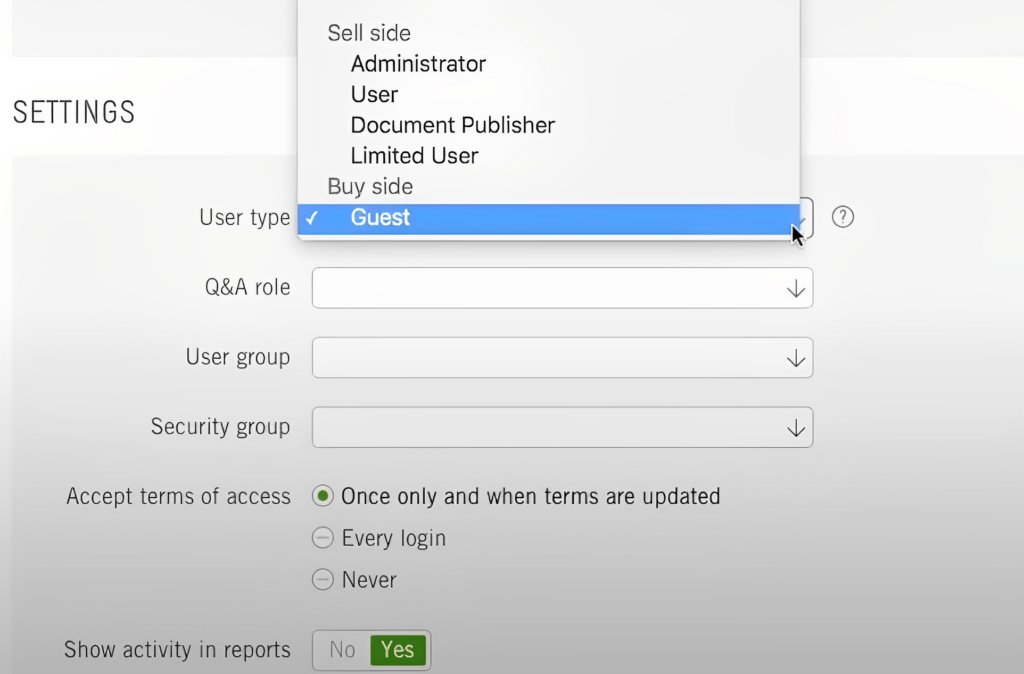
7. Invite third parties
As you’re approaching a business deal, you can invite potential buyers, partners, or authorities to the data room. Secure data room providers offer granular user permissions that allow you to control the levels of access requested users have.
Furthermore, admins can create groups according to users’ roles and allow them specific features and access levels. This way, project management becomes straightforward, secure, and efficient even if dozens of people are involved. And as a result, you can protect your files from any unwanted threats.
8. Control user activity and get insights
A virtual data room will provide you with reports that give you a clear view of the user activity. You can review these stats to detect suspicious behavior and avoid a data leak. Also, reports can provide you with useful insights on presenting your company better during the deal. And once the process you’re going through is over, you can study reports once again to see how you can improve the workflow during the next deal.
For in-depth and convenient tracking, the virtual data room provider should offer:
- Full audit trails in a print-friendly version for presentations at meetings
- Tracking with details about downloads, prints, views, and file view duration
- Group overview reports containing data on the number of logins, Q&A questions posted, permitted and accessed files
- Color-coded reports indicating the most active member groups and data rooms of the most interest
Rely on our expert choice – iDeals VDR
Visit WebsiteBest practices for building data rooms in 2024
Now that you know how to set up a data room, it’s time to learn the best practices for strengthening your data protection with security settings and better workflow management.
Implementing user permissions
To build data rooms that are security oriented, you need to decide on access rights for admins, corporate employees, investors, clients, financial advisors, and other third parties.
And since this task may seem tedious, we give you some examples of user groups and permissions. But note that they may differ depending on the deal and industry. However, the classic structure includes:
- Administrator. The document storage, user management page, and file permissions tab are completely under this person’s control. Admins can add documents, allow regular users to invite new users, hide members from each other, and generally control all processes in a data room.
- Management. Company managers usually have access to all data but aren’t assigned to any administrative obligations.
- Employees. Employees can be divided into access groups based on what documents they need for work. Typically, individual users or groups can upload files, edit content, share, and rename files.
- Finance. All financial documents must be available to users dealing with the financial side of the transaction.
- Investors. Potential investors need free access to tax information, balance sheets, income statements, and others related to the due diligence checklist. As for established investors, the VDR administrator must provide them access to strictly confidential information.
- Clients. Normally, this user group has access only to the client files and folders. However, specific access rights depend on the individual usage scenario.
Encrypting data
Data encryption is a security technique that encodes data and makes it visible only to someone with the right encryption key. Here are some tips on using encryption in your data room:
- Encryption at rest and in transit. There is no need to enable or disable encryption in transit — it is usually offered by default. However, some providers don’t offer encryption at rest by default and may require an extra procedure to enable it. You should contact your vendor’s customer service to clarify it.
- Customer-Managed Encryption Keys (CMEK). You can also get control of the encryption keys, which is an extra security measure called Customer-Managed Encryption Keys (CMEK). In particular, this option allows you to control data in the cloud infrastructure along with private encryption keys. In addition, you can choose where to store the encryption keys and the software for managing them.
Monitoring activity
Setting up activity monitors is essential, as you should have a tamper-proof audit record of all data room activities for corporate intelligence and defense against legal claims.
While audit trails are usually offered by default, you can set up automatic reports based on data room activity and enable real-time notifications:
- Automatic reports. One of the best monitoring practices is to keep key project managers in the loop by sending them customizable activity reports on specific recurring schedules. The recipients, in turn, can collect key intelligence by analyzing summaries of activities by a company and particular places in the data room, users, and access groups.
- Real-time notifications. Another valuable practice is real-time notifications, which allow the admin to know about the actions on a particular document. So, if a third party views, edits, downloads, or shares the same files multiple times, the admin will know about it instantly by receiving an email notification.
Virtual data room setup: Key takeaways
Now, let’s summarize key learnings from the article:
- Users may encounter challenges during data room preparations, such as compliance with regulations, user adoption, and permission settings.
- Properly setting up a virtual data room is essential to get the most out of its benefits — wish is not rocket science, as many data room providers offer a due diligence data room checklist which can be used to streamline preparation to due diligence or any other complex deal.
- Some of the best practices recommended for the efficient and secure use of virtual data room software include setting up user and file permissions, data encryption, and activity monitoring.
If you’re eager to explore more about data room providers — welcome to our main page and explore some of the best market expertise and the most secure data room providers in the industry.


